DoS attacks: What are the popular DoS attacking tools? (updated 2017)
DoS (denial of service) is a type of attack in which a threat actor sends bogus traffic to the targeted entity. The target is unable to distinguish between the attack traffic and legitimate traffic and ends up exhausting its resources towards attack traffic. This way the legitimate traffic gets denied of the resources rendering the target useless.
The attackers try to make the attack sophisticated by making the requests/traffic seem like normal traffic and making the frequency and source of traffic random.
e.g. if a website can handle 100 people/second clicking the signup button, an attacker only has to send 100 fake requests/second to make it so no legitimate users can sign up. This kind of attack can easily be controlled by blocking the IP etc. but when this is launched through a lot of different sources, mostly compromised PCs, this is called distributed denial of services or DDoS. This is tough to detect and block as the attacking sources are distributed among the legitimate users.
This is usually launched through a lot of compromised computes called “Zombies” and these are then used to send the requests without their knowledge. A complete network of zombies is also called a botnet which is used to launch other kinds of attacks as well.
Key reasons for attackers to do DDoS attack:
- Render a site useless
- Extortion/Ransom
- Revenge/hactivism
- Relatively simple to do with free tools
- Just for FUN
Consequences:
- Business loss
- Reputational loss
- Unsatisfied customers
- Loss of Infrastructure/equipment
- Unavailability or sluggish service
Categories of DDoS attacks
Volume based
The attackers send large volume of traffic/packets/requests to the target thus eating up all the resources. The requests choke the bandwidth and cause denial to other requests. Includes flooding attacks (ICMP and UDP).
Protocol based
Here the attacker targets the resources apart from bandwidth. The target here is servers, firewalls, IPS, other network equipment etc. The traffic is continuously processed leading to denial of services for legitimate requests.
Common attack types: - NTP amplification, Smurf attack, Fraggle attack, SYN floods, Ping of death etc.
Application layer attacks
These attacks are comprised of what appears to be legitimate application layer. ( layer 7) It sends requests to the server that are intended to crash/overflow it. The attackers can either overflow the application server with a large amount of requests or either block the resources of the server by sending extremely slow incomplete requests thus letting the sever wait for the complete request.
What is a DDoS Attack script and DDoS toolkit
DDoS attacks can be performed for various reasons explained above and are also performed by different set of people. The tools for this attack can either be written by the user as per need or are downloaded. Nowadays, DDoS is also available as a service offered by groups in the black-market. As per your subscription (e.g. 25Mbps/s on a particular target) DDoS attacks will be performed (Here's a resource that will navigate you through cyber security attacks).
- A DDoS attack script will either be written by a script kiddie or a white/black hat hacker whereas a DDoS toolkit will be written by professional black hat hackers.
- The intent of a dos script is to just perform the attack whereas a DDoS toolkit is a bundle of attacking script and penetration script.
- DoS script will bring down the application or a particular target whereas a DDoS toolkit will try to compromise the network and create zombies. These zombies can be used to launch DDoS programs or other attack campaigns.
- From an organisational perspective, attacks from a dos script can be easily detected and blocked as they are mostly launched from a single source but the real threat lies from ddos botnets. This does not mean that the attacks from dos tools are not harmful, the scripts are enough strong to bring down a medium size vulnerable application server.
- DDoS toolkits are specifically designed so that the compromised systems can be used to launch DDoS attacks and further create zombies. This becomes difficult to detect as the source is not one, the traffic seems to be legitimate and the systems are getting compromised. If the system gets compromised then there is a need to check for both outbound as well as inbound attacks.
Popular dos attacking tools
INTENT -Before starting an attack check a few questions.
- Do you want to take down the website or a complete network?
- Just choke up bandwidth?
- Create MAYHEM?
- Load test a server?
- Stress test a server?
Depending on the answers to the above questions you can select a tool.
TOOL considerations
- Is the tool a standard build or the work of a script kiddie or self-written?
- What is the target of the attack tool?
- Is the Tool capable of generating multiple types of DoS attacks?
- Can you customise the traffic as per need like NO of requests/sec and protocol selection?
- Is the tool easy to use? – Are you a command line fan or GUI lover
- Effectiveness? – Is the attack effective enough to be considered an attack or just high traffic
- Traffic patterns and stealth techniques used? – There is no point in using a tool if the attack traffic gets easily detected and blocked by conventional techniques. Is the tool using fragmentation and obfuscation techniques to hide the attack traffic?
DoS tool list
1. LOIC (Low Orbit ION cannon)
Open source DDoS tool which can easily perform TCP, UDP and HTTP DoS attacks. It has fairly simple GUI, the user just needs to know the target address/URL of the website and the attack which needs to be executed.
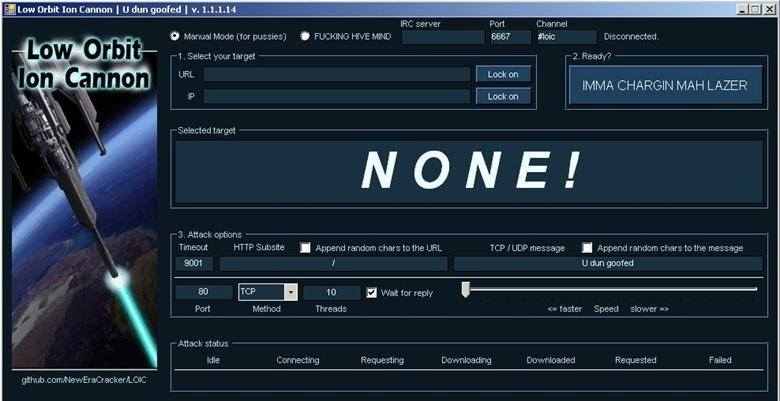
Image source: https://upload.wikimedia.org
GUI has been divided into 4 parts:
- Target selection (URl/IP)
- Ready state (Just for fun)
- Attack Options/Selection – Multiple connections are opened to the target server and messages are sent continuously to the target so that the target gets overloaded by the request and thus gets crashed. The speed of the request can be controlled by the slider bar, this can help the traffic hide in the regular traffic.
- UDP Attack: Select method - UDP. Port 80 set to default but can be changed as per need
- TCP Attack: Select the Method as UDP and rest is same.
- HTTP Attack: Select the method as HTTP.
- Attack status
- IDLE: No of idle threads
- Connecting, Requesting and Downloading: No of threads trying to connect to the target, No of threads connected to the server and now requesting for information or resources, No of threads which have started some download from the target after connecting and requesting
- Downloaded, requested and failed: No of times data download has been initiate, No of times a request has been initiated to the server, no response from the server is treated as failure.
Limitations
- Easy to find the attacker, IP address is exposed.
- Easily detected by the IDS/IPS/AV.
- Cannot perform DDoS attacks
- Cannot attack multiple targets at one time.
2. HOIC (High Orbit ION cannon)
This is a successor of LOIC and is again an open source DoS tool capable to attack 256 targets simultaneously. The attacking mechanism is same, it generates a large number of junk HTTP GET and POST request to overload the application server. The GUI is way too simple,
- Target: Target to be attacked
- Fire power – low, med, high (2,4 and 8 requests/sec respectively)
- Booster: To increase the power of the tool
- Status: Attack status
Users with limited or no knowledge can use this destructive tool and hence it becomes more dangerous.
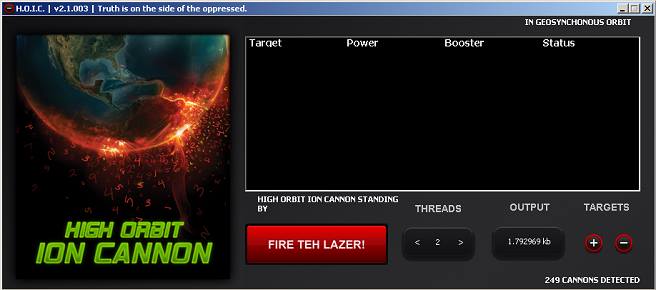
Image source: http://thanatos.trollprod.org/sousites/hoic/
Limitations
- Cannot generate TCP and UDP floods.
- Manual coordination among users is required to launch DDoS
- Source of the attack can be easily detected and blocked.
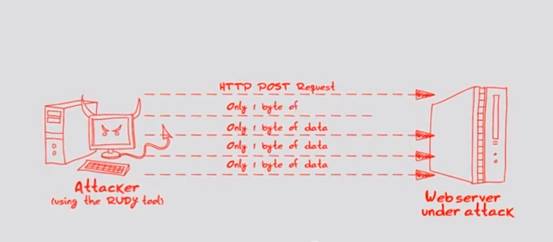
3. RUDY
Unlike flooding the server with a lot of requests, RUDY executes slow rate attacks. It detects if the website has any form field submissions. Upon identification, it sends a legitimate HTTP POST request with a long 'content-length' header field (prevents server from closing the connection) and then starts injecting the form with data, 1 byte at a time and that too at a slow rate (large time intervals between subsequent bytes). This causes a lack of application resources at the server thus denying legitimate requests.
Limitations
- Time consuming as the rate of attack is slow.
- Works only at layer 7(HTTP based)
- The website should have form submissions for the attack to work.
- Slow data can be detected as abnormal traffic and can get blocked.
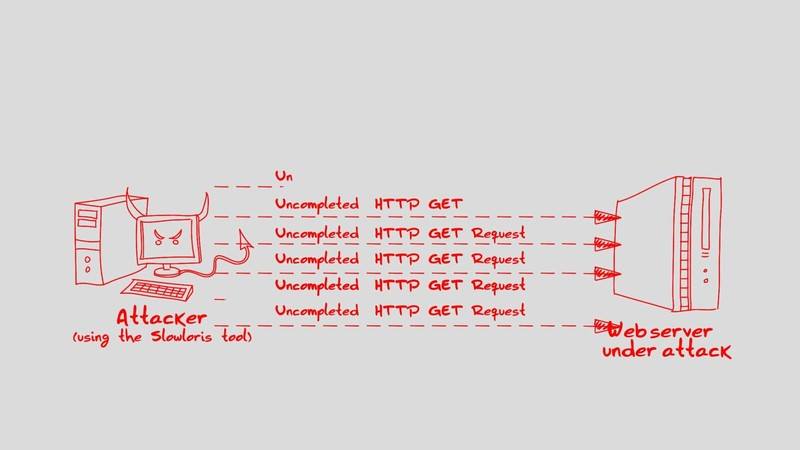
4. Slowloris
Slowloris is also a slow DoS attack script like RUDY. It sends HTTP GET request to the server but the request is not complete. Web server will wait for the request to complete and the resources are allocated. Parallel to this multiple threads of this kind are opened and thus the resources of the web server are exhausted. The attack script is also present in NMAP for testing the response of the webserver to the attack scenario.
Limitations
- Works only at layer 7(HTTP based)
- Slow data can be detected as abnormal traffic and can get blocked
- No advanced techniques to tweak the requests.
5. HTTP Unbearable Load King (HULK)
The main highlight of this tool is its capability to generate unique requests. The tool uses obfuscation techniques to generate unique requests. This helps in evading the conventional controls which can detect and block the abnormal traffic. This works well when you have behavioural analysis present in your network.
Feature set
- Traffic obfuscation, difficult to detect.
- Capability to hide/obfuscate source
- Forging capabilities for various fields in the web request.
Limitations
Traffic from HULK can be analysed and proper rules can be made to block the attack.
6. XOIC
XOIC is another fairly simple DDoS tool. The GUI is simple with limited fields
- Whois request functionality
- IP, port and protocol selection field
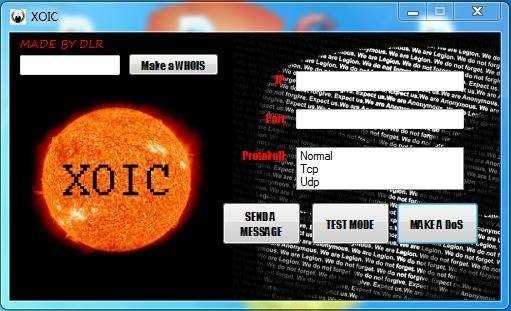
Image source: www.pentestingexperts.com
MODES
- Test
- DoS mode with TCP,UDP messages
Limitations
- No advanced features to hide the traffic.
- Easy to detect and block
7. DDoSIM (DDoS Simulator)
This tool is used to simulate a real world DDoS attack on both a website and network. The tool is written in C++ and has the capability to simulate the attack as if it is coming from a botnet by faking random IP addresses.
Feature set:
- Full TCP requests
- Layer 7 DDoS with valid requests
- Layer 7 DDoS with invalid requests
- TCP flooding
8. PyLoris
PyLoris is a python based tool that is used for testing services vulnerability to a DoS attack.
The methodology is simple – open full TCP connections and keep them open for as long as possible thus rendering denial to legitimate requests. Services that have
- Limit on the no of simultaneous TCP connections
- Handle connections in independent threads
- High memory allocation per connection
- Poorly managed connection strategy can be tested by this tool.
GUI is divided into 3 panes:
- General: Fields for host and port details
- Behaviour: Creating attack behaviour – no of connections, speed etc.
- Proxy: proxy type, port, credentials etc.
- Platform dependent
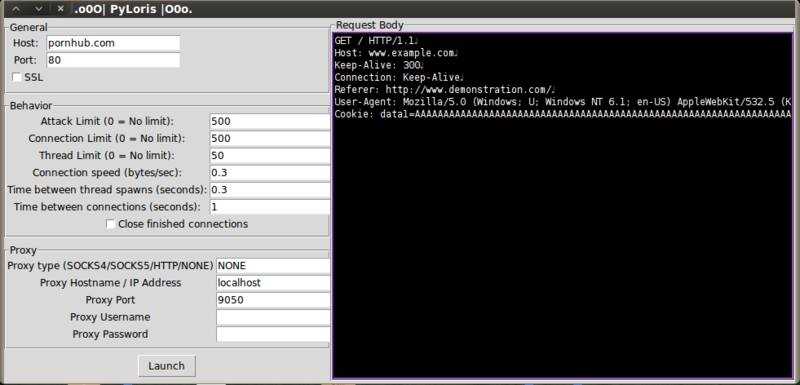
Image source: https://www.hackthis.co.uk
Limitations
- Python dependency
- Scripted tool, users might need help during installation and setup.
9. OWASP DoS HTTP POST
The tool has been created by ProactiveRISK for the OWASP(Open web application security project) to create awareness about application layer attacks. The tool is also used to do a performance testing and capacity planning of a webserver.
The tool a simple GUI which has 3 panes:
- Test type and destination: Define the URL or the target
- General parameters: Connection details and source details.
- Attacks parameters: Attack specific details
Once the attack is launched, behaviour of the target can be analysed. There should be a significant change in the no of requests coming and the resource allocation as well.
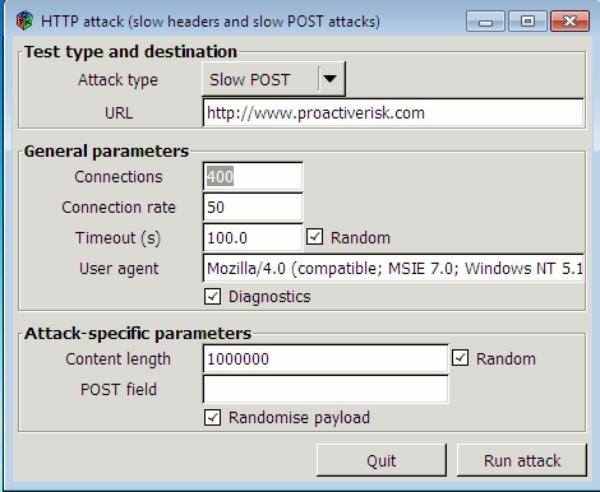
Image source: http://nguyencaotu.com
10. GoldenEye HTTP Denial of Service Tool
GoldenEye is a layer 7 DoS tool which has been developed in python. The tool tries to persist a socket connection by exploiting Keep-Alive and No Cache. This consumes all the HTTP/S sockets on the application server and thus causing DoS.
Features
- Random generation of user agents is possible
- Randomisation between GET, POST or random selection for a mixed traffic
Image source: toolswatch.org
Limitations
- Script based tool, Missing GUI
- Python dependency
- Platform dependency
DDoS Protection
- One very poor and expensive way is to beef up the server farm infrastructure to handle large no of requests and get a bigger bandwidth. This will handle both DDoS script attacks and volumetric attacks (also consider checking this perfect guide for cyber security certification).
- Rate limit the traffic: 15 request/sec from a single source can be a DDoS
- Set a threshold: Analyse your website over a period of time for the no of requests it experiences and the rate can be set accordingly, a buffer can be added in this for peak hours and low request times.
- Know the expected traffic: Do you expect UDP traffic? Get to know what type of traffic is legitimate and is expected by you and what not.
- Blocking the IP: Not a very good way since DDoS will have multiple sources and you might end up blocking the entire internet and blocking legitimate IP/user as well. Acceptable and practical upto a certain level.
- Have a plan to handle DDoS and related incidents.
- Get professional DDoS mitigation services
- Deploy SOC team for aggressive monitoring of the events and take actions in time
- Know the threats: present and emerging.
- Drop Packets from Obvious Sources of Attack: IP blacklists and botnet databases
- Follow whitelisting approach wherever possible. Ex server to server connection
- Proper configuration of network firewalls and routers: Simpler attacks can be handled here itself.
- Ensure that PC and network devices are upto date and free from vulnerabilities.
Conclusion
- DoS attacks have been in news every now and then, the result is mostly unavailability of the websites or other services. It affects both business and reputation. The art of the attack lies in how to evade attack detection and blocking tools and reach the target with bogus requests. Since attackers are coming up with new tools and techniques to achieve this, organisations need to update themselves with the attacks, trends and mitigation strategies. If the mitigation strategies fail there must be an incident management plan in place.
- For security enthusiast’s and security operation teams/individuals – you are expected to know atleast the basic concepts of the attack(s), a few known tools and a little about the traffic types they create. This will help in security monitoring of the traffic and also creating effective rules for blocking unwanted traffic.
- For a CEH, you are expected - to know the attacks in theory and practical is very important. They are required to monitor and dissect the traffic to ensure that their actions do not block legitimate users. For this, they should have a clear understanding of how the attack tools work, their traffic patterns and impact they can have on the organisation if not detected on time. If you are about to give the exam, ensure that you are ready with the attack concepts, working of various tool and other concepts like zombies, DDoS toolkits etc.
Get trained by experts. Register Now!
