SPECTRE and MELTDOWN: How do I know if my PC is at risk?
2018 has started with two new vulnerabilities that have targeted the hardware and not the software. The exploitable hardware if from Intel who are the giants in chip making market and hence the news has spread like forest fire. In this article we will be covering a few things – What a Kernel is, a few architecture level concepts which will help us in understanding the vulnerabilities better, followed by technical explanations of spectre and meltdown, their similarities, risk associated, affected processors and patch status. So let’s start.
Kernel is a program which manages the interaction between software and hardware components. Kernel is present in laptop, desktop and mobiles as well. Let’s consider the case of a mobile; a camera application needs the following accesses
- Camera (to click pictures)
- RAM ( to run the application)
- ROM (To save the captured pictures)
And some other permissions depending on the functionality. Who uses what, do they have the permissions available to access the resource, what is the priority in which the resources will be granted to the processes. This all is governed by the Kernel. Spectre and meltdown are the vulnerabilities present the system which allows criminals to steal sensitive information form devices.
Branch Prediction and Speculative execution
To understand this let’s take a general example.
A man goes to a restaurant at 8:00AM for having breakfast and orders an omelette. The order takes 5 minutes to prepare and he is served at 8:07AM. The same pattern is followed each day. The chef takes a note of the routine and prepares the omelette ahead of time as he is expecting the customer. This way the costumer is getting his breakfast quickly. Now let’s assume that nay of the below happens:
- The customer did not turn up
- Orders a different dish from the menu
In either case the chef needs to throw away the omelette and prepare a new dish.
In case of a compute the kernel performs a lot of calculations beforehand as the results are expected in the course of a running program. This speeds up the execution time. This process of guessing and performing the calculations beforehand is called branch prediction and speculative execution. If the results are not needed the results are thrown away. This gets stored in an unsecured part of the cache memory where unauthorised users can access this through side channel attacks.
SPECTRE
As per dictionary, spectre is a ghost, something which is widely feared and cannot be controlled. The vulnerability has been named spectre as it’s going to be around for a while with little or no full proof mitigation.
With speed being the prime focus, a modern processor wants to execute processes and instructions fast but the memory space is limited and may not be free for the processes, the processor instead of waiting for the memory to get free speculates the next instruction and generates the expected result.
Let’s consider this with the help of an example. We have two instructions below, the value of x will decide the value of Y, but Y cannot be calculated if the memory is not available.
X+1=y //Instruction 1
Y+2=Z //Instruction 2
Now the processor speculates the value of Y and processes Instruction 2 for the value of Z. The result can either be correct or wrong. Once the memory if free, the processor will check if the speculation is correct , if yes the value of Z is committed else the result is discarded. Now the question is, how does the processor decides what value of Y or X to speculate?
Let’s take another example:
If(x< array[1]) //Instruction 1
Y=array2(array[x]) //Instruction 2
Attacker sends some value of X (correct values which will cause the execution of instruction 1 and 2):
This is done to train the processor so that speculative execution kicks in. This is done multiple times so that processor understands the pattern and starts to execute the next statements (also consider checking out this perfect parcel of information for cissp certification).
Now the attacker sends malicious value of X which is greater than array1. The next instruction is executed for the malicious values and stored in the memory which the attacker can steal via side channel attack. The processor will check this later when the memory is allocated that the result needs to be discarded but at that time the memory is already being leaked.
MELTDOWN
Meltdown allows attackers to read arbitrary physical memory (including physical memory) from an unprivileged user process. It uses Out of order instruction execution to leak data via a processor covert channel (unintended data transmitting route). What is out of order instruction execution? – Instructions are not executed in a serial order – Instruction 1, then 2 and then 3 but in a random order.
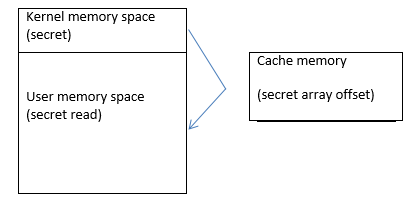
To understand Meltdown in detail, let’s first understand the memory block.
Memory layout
In general, a user process cannot access kernel space. Any interaction required is done through a mapping concept called page tables. If the user space tries to directly access kernel space, an exception is triggered. So there is a virtual wall between the kernel space and he user space.
In order to prevent the memory to be leaked, we do not want the attackers to find out the details of the address space and hence the processors have been using ASLR: Address space layout randomisation. This has been implemented in the user memory but not in the Kernel memory space except in Linux.
In meltdown attack the attackers first launch a process. Inside that process the attackers are going to create a large user space array. The users process is going to read an arbitrary kernel memory, this is going to cause an exception. But this read is constructed in a way that the read will happen out of order and the secret data is present in the user space for sometime and the array offset is present in the CPU cache. Now even though the secret data is written in the user space for a brief time, this cannot be read as it gets washed out by the CPU before it is read. The idea here is that we are going to get the value by hitting the CPU cache. After each instruction the cache is flushed and then after the operation the cache is read. The cached element will be returned much faster, revealing the contents of the secret byte read. This way we are leaking 1 byte of memory and this can be repeated multiple times to get the secret data.
You may also like: https://www.greycampus.com/blog/information-security/what-are-the-best-password-cracking-tools
How are Spectre and Meltdown alike and different?
| MELTDOWN | SPECTRE | |
|---|---|---|
| Practical attacks against | Intel | Intel, AMD, ARM |
| Allows Kernel memory read | YES | NO |
| Patched with KAISER patch | YES | NO |
| Leaks arbitrary user memory | YES | NO |
| Remotely executable | Maybe | NO |
| Most likely to impact | Kernel integrity | Browser memory |
Why this is a risk now?
Previously the computers were self-contained and there was no way to see the data being thrown away hence there was no risk. Today the systems are connected to each other and share system resources including memory. When discarded data from speculative execute on gets stored in shared memory criminals find a way to get in and hijack the data. The computers can be tricked to load any data into this shared memory so they can steal it.
What is the problem INTEL is facing?
Intel CPUs implement TSX (Transactional Set Xecution) which allows grouping of instructions for all or nothing execution. Either all instructions will execute or nothing. It’s just like a transaction. You cannot clear the credit card bill if you do not check for the available balance. This TSX causes the exploitation to be five times faster and since INTEL is a leader when it comes to processors the issue becomes more critical (also consider checking out this career guide for Cyber security jobs).
You may also like: https://www.greycampus.com/blog/information-security/top-security-certifications
How do I know if my PC is at risk?
Chip designs from Intel, ARM and AMD are susceptible to some form of the attack, Apple, Google, Microsoft, Amazon AWS all have the same chip structure and hence are all affected by this. Intel has release a full list of processors which are being affected by this vulnerability, If you are using any of the below you are also affected by the flaw:
- Intel Core i3 processor (45nm and 32nm)
- Intel Core i5 processor (45nm and 32nm)
- Intel Core i7 processor (45nm and 32nm)
- Intel Core M processor family (45nm and 32nm)
- 2nd generation Intel Core processors
- 3rd generation Intel Core processors
- 4th generation Intel Core processors
- 5th generation Intel Core processors
- 6th generation Intel Core processors
- 7th generation Intel Core processors
- 8th generation Intel Core processors
- Intel Core X-series Processor Family for Intel X99 platforms
- Intel Core X-series Processor Family for Intel X299 platforms
- Intel Xeon processor 3400 series
- Intel Xeon processor 3600 series
- Intel Xeon processor 5500 series
- Intel Xeon processor 5600 series
- Intel Xeon processor 6500 series
- Intel Xeon processor 7500 series
- Intel Xeon Processor E3 Family
- Intel Xeon Processor E3 v2 Family
- Intel Xeon Processor E3 v3 Family
- Intel Xeon Processor E3 v4 Family
- Intel Xeon Processor E3 v5 Family
- Intel Xeon Processor E3 v6 Family
- Intel Xeon Processor E5 Family
- Intel Xeon Processor E5 v2 Family
- Intel Xeon Processor E5 v3 Family
- Intel Xeon Processor E5 v4 Family
- Intel Xeon Processor E7 Family
- Intel Xeon Processor E7 v2 Family
- Intel Xeon Processor E7 v3 Family
- Intel Xeon Processor E7 v4 Family
- Intel Xeon Processor Scalable Family
- Intel Xeon Phi Processor 3200, 5200, 7200 Series
- Intel Atom Processor C Series
- Intel Atom Processor E Series
- Intel Atom Processor A Series
- Intel Atom Processor x3 Series
- Intel Atom Processor Z Series
- Intel Celeron Processor J Series
- Intel Celeron Processor N Series
- Intel Pentium Processor J Series
- Intel Pentium Processor N Series
How do I stay safe?
- Install the software patches which chipmakers are coming up with. Prioritise the systems for criticality and plan for installing the patches. Keep the plan ready as the companies are working to roll out the patches soon. Patch the critical ones first followed by the less critical ones. Be sure to test the patch for stability as the companies might miss something considering the urgency.
- Keep your antivirus updated – Keep your system free from malwares.
- Keep your browser and other software updated.
- Do not get Phished – Do not let yourself tricked into clicking suspicious links or downloading malicious software.
Patch status
Microsoft has released the patch KB 4056892 for Spectre and meltdown, but unfortunately many users have reported problems after updating the patch. Users have reported repeated system reboots or unable to reboot the system and even bricking the AMD processor. Even reinstalling the windows is not an option now.
Intel has recommended not to apply the current version of the patch. Intel has come up with a detailed technical note on “Speculative execution side channel mitigation”.
Intel has come up with multiple statements when it comes to judging the effect of the performance of the CPU after the patch has been applied. First response, performance impacts are workload dependent and will not be significant to the clients.
Second response, Performance impacts may be higher. CPU could be affected by applying the patch and there could be a slowdown of anywhere between 5% - 30 %.
The patch should have least effect on the performance for client PC and gaming PC but the impact will be noticeable in case of servers. This is concern for most of the companies as Intel dominates the server market. Some companies have tested their infrastructure for performance monitoring before and after the patch. This is one of the ways to be sure about the performance drop if there is any. Although the numbers cannot be considered a benchmark as the load is different for different organisations. In short, yes there will be an impact on the PC, it might be negligible or significant is what cannot be confirmed now.
What's next in Cyber Security?