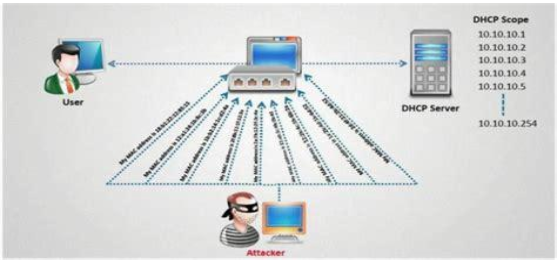
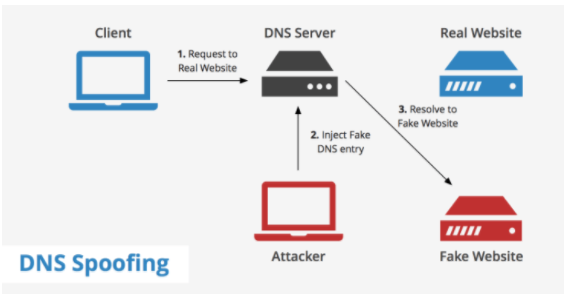
Dynamic Host Configuration Protocol (DHCP) is used to assIP's DHCP-enabled clients. The server holds valid TCP/IP configuration parameters, valid IP addresses and time period of the lease offer. When a client needs an IP, it sends a request to the DHCP server. The DHCP server asks the client to send the required parameters and once it receives the parameters, DHCP server sends the acknowledgement which contains the IP address of the client. Source: http://l4wisdom.com The DHCP client requests an IP address by broadcasting a DHCP Discover message to the local subnet. The client is offered an address when a DHCP server responds with a DHCP Offer message containing an IP address and configuration information for lease to the client. The client indicates acceptance of the offer by selecting the offered address and broadcasting a DHCP Request message in response. The client is assigned the address and the DHCP server broadcasts a DHCP Ack message in response, finalizing the terms of the lease. When the client receives the acknowledgement, it configures its TCP/IP properties by using the DHCP option information in the reply and completes its initialization of TCP/IP. Source: https://www.briefmenow.org/ec-council/how-do-you-defend-against-dhcp-starvation-attack-2/ It’s a denial of service attack, an attacker sends forged DHCP requests to the server and leases all the available IP’s thus the legitimate clients will not get an IP assigned; or the Attacker may send bogus request/replies luring the client to connect to attacker’s machine instead of valid DHCP server. Source: https://www.keycdn.com/support/dns-spo Here the attacker sends fake DNS packets to the server, thus causing fake entries in the DNS table for the target website. So when a client sends a request to the website, DNS server resolves the domain to IP using injected DNS records and redirects the user to a Fake or malicious website intended by the attacker. Enable Port security. DHCP snooping binding must be enforced. Use HTTPS instead of HTTP. Use SFTP instead of FTP. Use SSH instead of telnet. Avoid using clear text protocols. Always encrypt the wireless traffic using WPA2. Check whether NIC’s running in promiscuous mode. Implement DNSSEC. Use Firewall. Cain and Able Yersinia for DHCP starvation Wireshark
DHCP Poisoning
Introduction
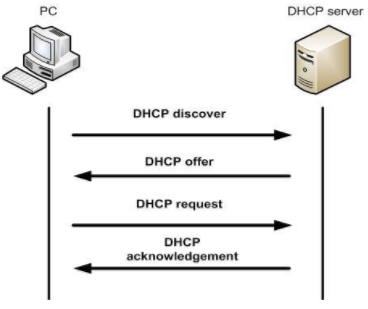
DHCP Starvation attack:
DNS poisoning attack:
Countermeasures:
Some tools: