IDS: Intrusion Detection System
IDS’ are the security systems which monitor the traffic and alert or notify the administrator on traffic of concern. They do not prevent the attack but they just alert the administrator.
Types:
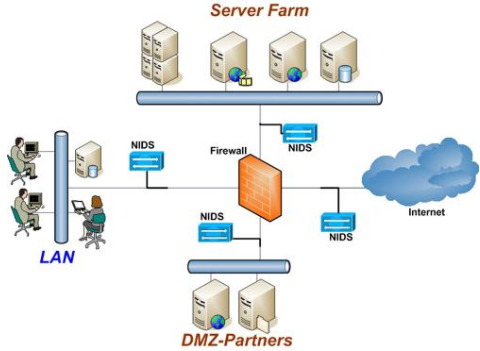
Network-Based IDS:
IDS can be installed at the perimeter of the network- on LAN, on subnets, on the important server, etc. The organisation can be centralised where the agents are installed on all major entry points, and all these agents send their log/report to the centralised manager who takes the decision; or it can be in distributed mode, where each agent has some decision making capability and the centralised manager takes complex decisions.
Host-based IDS:
It is a tedious process to install IDS on all host machines.
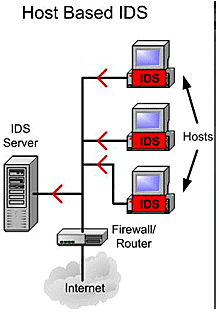
Image Source: https://www.hackthis.co.uk/articles/basics-of-intrusion-detection-systems