Wireless networks come with excellent advantages- connectivity beyond walls, wireless connection, easy to access internet even in areas where laying cables is difficult, speed and sharing. But, wireless networks have a few disadvantages, the major issue being- the questionable security. Access Point: The point where the mobile device, computers connect to the wireless network. SSID: Service Set Identifier identifies the access point, it is a human-readable text which when broadcasted leads to the identification of an access point. BSSID: Mac address of the Access point. Bandwidth: Amount of information that can be transferred over the connection. There are various standards for wireless transmission: When a client wants to connect to an open access point he/she sends a probe request, and the AP sends a probe response; the client then sends an authentication request. Upon receiving a response, the client establishes an association with the AP. Here, the client sends a probe request, and the access point sends the probe response; then, the client requests for an authentication request, the AP sends an authentication challenge to the client. The client needs to send the shared key as authentication challenge response. AP, then, verifies the client and authenticates him/her, who then establishes a connection with the access point. In the corporate environment, instead of an Access point verifying client’s authentication details, a centralised server does the job of verifying the client. RADIUS is a centralised authentication server which verifies clients who want to connect with the access point.
Introduction to Hacking Wireless Networks
Important Terms:
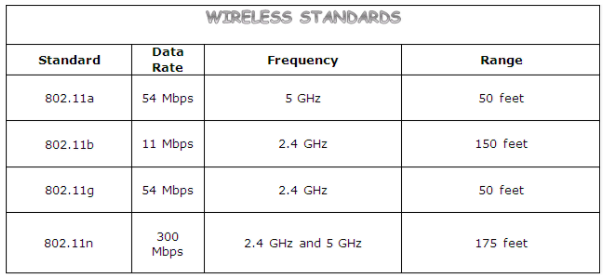
Source: http://www.computer-networking-success.com/wireless-networking-basics.html#sthash.tihe8vJl.dpbs
Authentication:
Open Authentication:
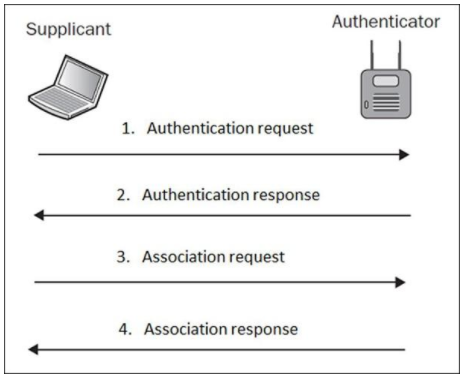
Source: https://www.tutorialspoint.com/wireless_security/wireless_security_wifi_authentication_modes.htm
Shared Key Authentication Process:
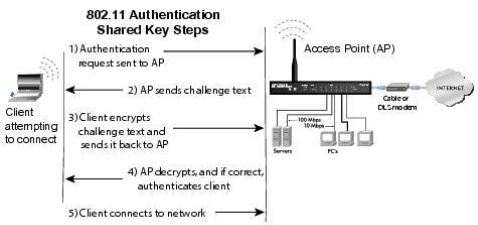
Centralised Authentication:
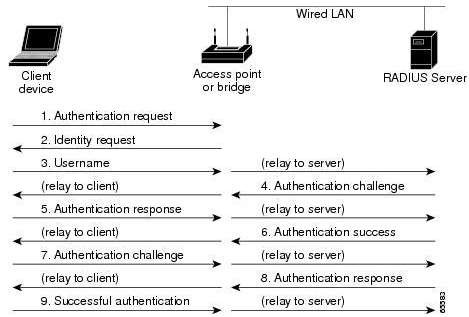
Image Source: https://www.cisco.com/c/en/us/td/docs/routers/access/wireless/software/guide/SecurityAuthenticationTypes.html