TCP guarantees delivery of data, and also guarantees that packets will be delivered in the same order in which they were sent. In order to guarantee that packets are delivered in the right order, TCP uses acknowledgement (ACK) packets and sequence numbers to create a "full duplex reliable stream connection between two endpoints", with the endpoints referring to the communicating hosts. The connection between the client and the server begins with a 3-way handshake. After the handshake, it is just a matter of sending packets and incrementing the sequence number to verify that the packets are getting sent and received. The goal of the TCP session hijacker is to create a state where the client and server are unable to exchange data; enabling him/her to forge acceptable packets for both ends, which mimic the real packets. Thus, the attacker is able to gain control of the session. Source: https://www.owasp.org/index.php/Session_hijacking_attack IP Spoofing: IP spoofing is a technique which is used to gain unauthorized access to computers where the intruder sends a message to a computer with an Ip address indicating that the message is coming from a trusted host. Man in the middle Attack: Attacker tries to get the session Id by doing ARP spoofing and man in the middle attack. Source: http://slideplayer.com/slide/6005679/ Blind Hijacking: In cases where source routing is disabled, the session hijacker can also use blind hijacking where he injects his malicious data into intercepted communications in the TCP session. It is called blind because he cannot see the response; though the hijacker can send the data or commands, he is basically guessing the responses of the client and server. UDP session Hijacking: UDP is a connectionless protocol. UDP/IP provides very few error recovery services offering. There is no direct way to send and receive datagrams over an IP network. Therefore, the delivery integrity, non-duplication and orders are not guaranteed. UDP doesn't use sequence numbers like TCP, it is mainly used for broadcasting messages across the network or for doing DNS queries. Using secure protocols instead of clear text protocols like HTTP, FTP.Telnet, Rlogin, etc. Encrypting session id will increase the complexity of the session id prediction. Sending session id over SSL. Use long random numbers for session id. Implement timeout for the session when the session is logged out, or session id expires. Having different session id for each page. Use switches rather than hubs. Ensure server side and client side protection software. Use IDS for detecting ARP spoofing/Poisoning. Do not click on suspicious links. Check the web application for all errors. Using IPSec is a valid defence mechanism.
Network or TCP Session Hijacking
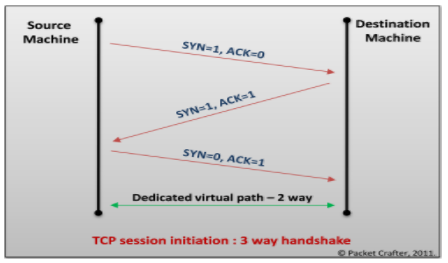
Image Source: http://www.bvkmohan.com/2011/02/tcp-flags-hackers-playground-and.html
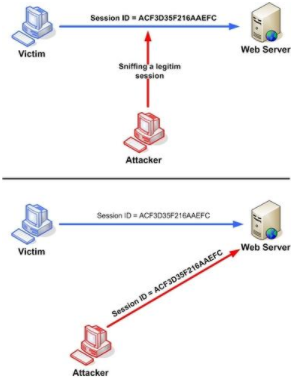
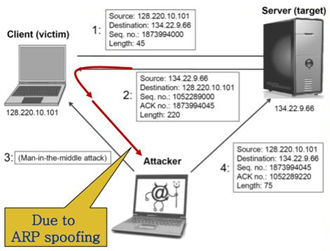
Counter Measures: