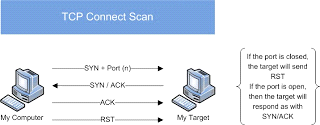
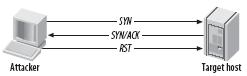
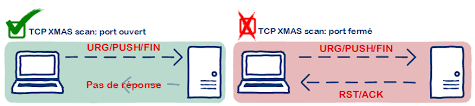
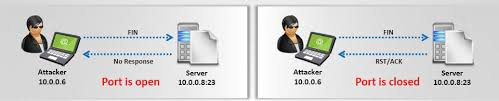
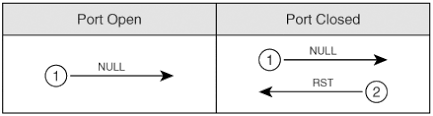
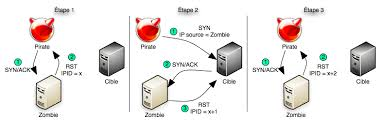
We have various types of scan: Connect scan: Identifies open ports by establishing a TCP handshake with the target. Nmap command: nmap -sT -v -p- <TargetIP> Half-open scan otherwise known as Stealth scan used to scan the target in a stealthy way by not completing the TCP handshake by abruptly resetting the communication. Source: https://www.safaribooksonline.com Nmap command: nmap -sS -v <TargetIp> XMAS scan: This is also called as inverse TCP scanning. This works by sending packets set with PSH, URG, FIN flags. The targets do not respond if the ports are open and send a reset response if ports are closed. Source: https://www.information-security.fr FIN scan: Fin flag is set in the TCP packets sent to the target. open ports doe does not respond while closed ports send a reset response. Source: https://securitcrs.wordpress.com Nmap command: nmap -SF <targetIp> ACK scan: Here the attacker sets the ACK flag in the TCP header and the target's port status is gathered based on window size and TTL value of RESET packets received from the target. Source: https://www.hackingloops.com Nmap command: nmap -SA -v <targetip> Null Scan: Works by sending TCP packets with no flags set to the target. Open ports do not respond while closed ports respond with a RESET packet. Nmap Command: nmap -sN -p- <targetIP> Idle Scan: Here the attacker tries to mask his identity uses an idle machine on the network to probe the status details of target ports. Source: https://en.wikipedia.org/wiki/Idle_scan Nmap command : nmap -Pn -sI ZombieIp TargetIp Banner Grabbing Banner grabbing is a process of collecting information like operating system details, the name of the service running with its version number etc. Vulnerability scanning: Mainly automated tools are used for this purpose. These automated scanners scan the target to find out vulnerabilities or weakness in the target organization which can be exploited by the attackers. Vulnerabilities include application vulnerabilities, configuration vulnerabilities, network vulnerabilities, operating system vulnerabilities etc. Some examples include operating system is not updated, default passwords used, plain text protocols used, vulnerable protocols running etc. Tools: Nessus, Acunetix Draw Network Diagrams With the information gathered, the attacker can come up with a network diagram which might give him information about network and architecture of the target organization helping him to identify the target easily Tools: Network View, Opmanager etc Prepare Proxies Proxies can use to maintain the anonymity of the attacker by masking the IP address. It can capture information passing through it since it acts as an intermediary between client and server and the attacker can access the resources remotely using the proxies. Eg: TOR browsers, Onion sites etc, Proxify, Psiphon etc Countermeasures: Configure IDS and firewall to block probes. Keep firewall, routers, IDS firmware update Run port scanners to verify the security of the target. Add rules in firewall restricting access to ports. Disable ICMP based scanning at firewall.
Scanning Methodology

Loading...