Security, Functionality and Usability Triangle
There is an inter dependency between these three attributes. When security goes up, usability and functionality come down. Any organization should balance between these three qualities to arrive at a balanced information system.
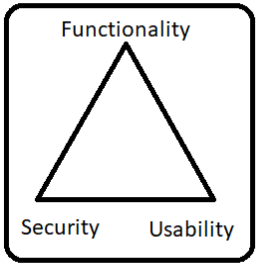
Some important terms to consider in hacking are
Threat: Anything that has potential to cause harm. There are various threats available to system threats, Network threats, application threats, cloud threats, malicious files threats etc.
Vulnerability: A weakness or a flaw in the system which an attacker may find and exploit. An updated OS, Default Passwords, Unencrypted protocols are all good examples of vulnerabilities.
Attack: Method followed by a hacker/Individual to break into the system. Denial of service attack, Misconfiguration attacks, Operating system attacks, Virus, and Worms are all example of Attacks.
Attack vectors: Path or means by an attacker gains access to an information system to perform malicious activities.