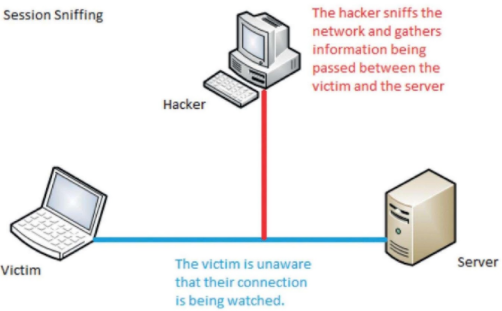
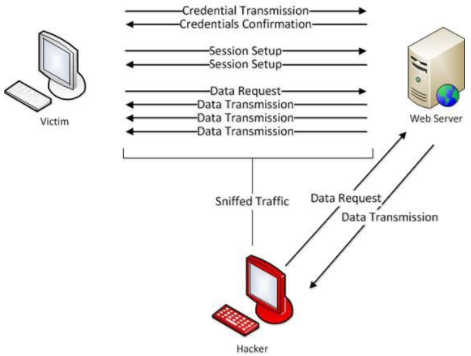
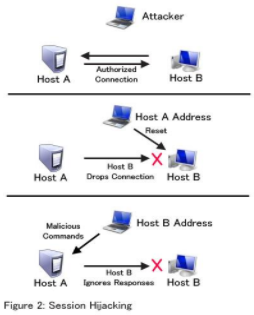
Session hijacking is defined as taking over an active TCP/IP communication session without the user’s permission. When implemented successfully, attackers assume the identity of the compromised user, enjoying the same access to resources as the compromised user. Identity theft, Information theft, stealing sensitive data are some of the common impacts of session hijacking. Source: http://techgenix.com/understanding-man-in-the-middle-attacks-arp-part3/ There are two types of session hijacking depending on how they are done. If the attacker directly gets involved with the target, it is called active hijacking, and if an attacker just passively monitors the traffic, it is passive hijacking. The attacker will silence one of the machines, usually the client computer, and take over the clients’ position in the communication exchange between the workstation and the server. The active attack also allows the attacker to issue commands on the network making it possible to create new user accounts on the network, which can later be used to gain access to the network without having to perform the session hijack attack. Source: https://www.hackingloops.com/session-hijacking-how-to-hack-online-sessions/ In Passive session hijacking attack, the attacker monitors the traffic between the workstation and server. The primary motivation for the passive attack is to monitor network traffic and potentially discover valuable data or passwords. Source: https://www.malwarefox.com/session-hijacking/
Session Hijacking and its Types
Introduction
Types of session hijacking attacks:
Active:
Passive: