Source: https://www.slideshare.net/teknetir/cehv9-module-10-session-hijacking The first step in the session hijack attack is locating a target user. Attackers look for two things prior to their attack- first, they look for networks that have a high level of utilization; high volume networks help attackers to remain anonymous and they also provide a healthy supply of users to choose from, which also helps the attack. Secondly, users who use insecure network protocols such as Telnet, rlogin (remote login), and FTP (file transfer protocol) are easy targets due to their inherently insecure design. Packet sniffing software can be used to sniff network traffic for the purpose of locating vulnerable protocols like FTP, Telnet, and rlogin. Port scanning software can also be used to identify servers that have FTP, Telnet, or rlogin ports open. The attacker then finds an active session between the target and another machine and places himself between them. Using a sniffer like Wireshark, he captures the traffic and tries to gather information about the session. He then monitors the traffic for vulnerable protocols like HTTP, telnet, rlogin, etc., and tries to find any valid authentication packets passing through. The attacker tries to predict the session id using available information. Now that a target has been chosen, the next step in the session hijacking process is sequence number prediction. Sequence number prediction is a critical step because failing to predict the correct sequence number will result in the server sending reset packets and terminating the connection attempt. If the attacker guesses the sequence numbers wrong repeatedly, the likelihood of detecting the attack increases. In application-level hijacking, active attacks are pursued to steal the session Id. Man in the middle attack, cross-site scripting, sniffing are used to steal the session id. Brute Forcing: This is a time-consuming process. While sequencing number guessing can be done manually by skilled attackers, software tools are available to automate the process. Once a session is chosen and sequence numbers predicted, one of the targets has to be silenced. This is generally done with a denial of service attack. The attacker must ensure that the client computer remains offline for the duration of the attack, or the client computer will begin transmitting data on the network causing the workstation and the server to repeatedly attempt to synchronize their connections; resulting in a condition known as an ACK storm. The final phase of the session hijack attack entails taking over the communication session between the workstation and server. The attacker will spoof their client IP address, to avoid detection, and include a sequence number that was predicted earlier. If the server accepts this information, the attacker has successfully attacked the communication session.
Session Hijacking Process
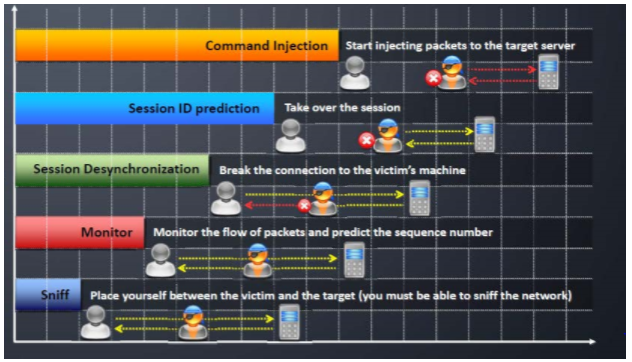
1. Sniffing into Active Session:
2. Monitor:
3. Session Id Retrieval:
4. Stealing:
5. Take One of the Parties Offline:
6. Take over the Session and Maintain the Connection: