The attacker sends some malicious query to the database which results in errors. The errors should be very generic, otherwise, they may give useful hints to the attacker. Comment-Line: Using comment line to cause the database to ignore a part of a valid query. E.g. Select * from stores where product_id = blah’ or 1=1-- (everything after this will be neglected) Tautology: There are a lot of strings which always evaluates to be true, like ‘1’ = ‘1’ ‘a’ = ‘a’, etc., using them in the query to create constantly true conditions. E.g. Select * from users where username=’blah’ or ‘a’=’a’ -- and password=’pass’ Using union command in SQL query to execute additional queries; thereby, modifying/inserting/deleting or dropping the contents of the table. E.g. Select * from stores where product_id=1 union select 1,database(),user(),4# Stored procedures: Creating malicious inputs to execute malicious queries. Incorrect queries: Coming up with logically incorrect queries to see the error messages to get more information about the target database. Select * from stores where id=1’ The above query will result in a syntax error and might reveal the backend database type. This is a type of SQL injection where we don’t have a clue as to whether the web application is vulnerable to injection attack or not. Boolean: Only correct queries show the result, wrong queries do not return anything. Attackers should try to generate logically correct queries. If suppose the original query to the database is Select * from users where id=’id.txt’ If we give blah’ and 1=1# as input which evaluates to be a right query Select * from users where id=’blah’ or 1=1#, we will see the user results. If we give blah’ and 1=2# as input which is a wrong query then we don’t see any results. Select * from users where id=’blah’ or 1=2# Time delay: Depending on some conditions, setting a time delay. If that condition is satisfied, we can observe the time delay; thereby, concluding that the input we gave produced a positive result. This is a time consuming process. SQLMAP, Marathon tool. Use encryption. Obfuscate string to avoid pattern matching. Use Concatenation to confuse the IDS. Use encoding like ASCII encoding, hexadecimal encoding to avoid detection. Insert inline comments between query.
Types of SQL Injection
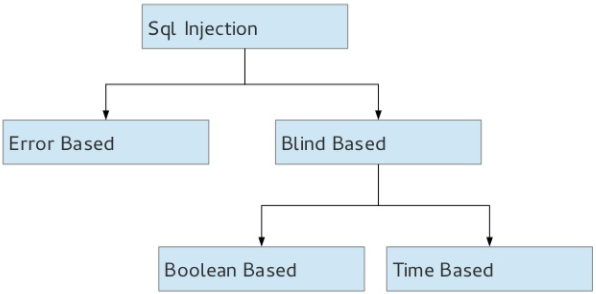
Error based Injection:
Union Based SQL injection:
Blind SQL injection:
Types:
Tools:
Perimeter tools (IDS) Evasion Techniques: