A database containing all patterns will be matched against incoming packets. When a match is found, the IDS alerts the administrator. The present scenario of traffic is compared to the baseline version, the administrator is notified of any peak differences. If there are any deviations in the way a protocol is functioning at the entry points, the administrators are notified. Sending more packets to IDS, and fewer packets to the internal network or target; thus, causing IDS to miss the pattern. Sending fewer packets to IDS and more packets to target, the IDS may accidentally drop few packets; thus, it may not be able to recognise the attack pattern but when the packets enter the target they become an attack. Encryption: Encrypted text cannot be recognised by IDS Encoding: By Using various encoding techniques like ASCII encoding, hexadecimal encoding, etc. Using Obfuscated codes Taking advantage of reassembly timeouts of IDS: Sending a large number of fragmented packets to IDS may cause a DOS kind of attack on IDS; thus, bypassing IDS. Honey bot: It’s a trap to research and understand the attacker’s behaviour on the network. Either the honey bot can be designed as high interaction one, allowing the attacker to completely compromise all services; thus, studying the pattern and attack methods, or designing a low interaction one, where only limited services are opened for attackers to compromise. The basic need is to study the attack pattern and update the signature database for new signatures and patterns.
Ways of Detecting Attacks
Signature-based:
Behaviour Based:
Protocol anomaly based:
Evasion Techniques:
Insertion Attacks:
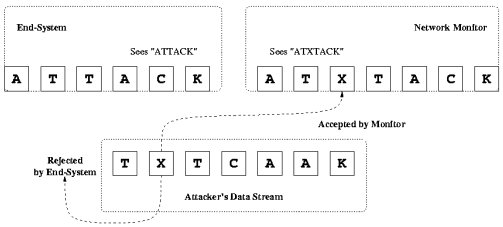
Image Source: http://insecure.org/stf/secnet_ids/secnet_ids.html
Evasion Technique:
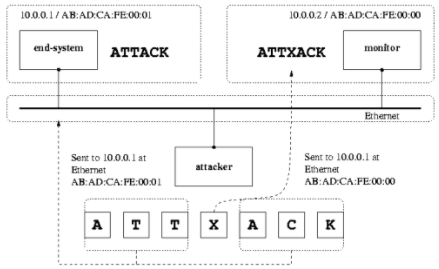
Image Source: http://insecure.org/stf/secnet_ids/secnet_ids.html