Websites are hosted on web servers. Web servers are themselves computers running an operating system; connected to the back-end database, running various applications. Any vulnerability in the applications, Database, Operating system or in the network will lead to an attack on the web server. Vulnerability stack of a web server is given below (source: White hat security) Source: http://black-shado.blogspot.com/2006/11/vulnerability-stack.html E.g. IIS and Apache An attacker may cause a denial of service attack by sending numerous service request packets overwhelming the servicing capability of the web server, or he may try to exploit a programming error in the application causing a DOS attack. E.g. buffer overflow attack, SYN flooding, HTTP get Request Flooding, Ping of death. SQL injection attacks are used to deface the website. When an attacker finds out that input fields are not sanitized properly, he can add SQL strings to maliciously craft a query which is executed by the web browser. He may store malicious/unrelated data in the database; when the website is requested, it will show irrelevant data on the website, thus displaying a defaced website. This is vulnerability where an attacker is able to access beyond the web root directory from the application. If he is able to access beyond web root directory, he might execute OS commands and get sensitive information or access restricted directories. If unnecessary services are enabled or default configuration files are used, verbose/error information is not masked; an attacker can compromise the web server through various attacks like password cracking, Error-based SQL injection, Command Injection, etc. An attacker may redirect the victim to malicious websites by sending him/her a malicious link by email which looks authentic, but redirects him/her to malicious web page thereby stealing their data. There are a lot of other web application attacks which can lead to a web server attack- Parameter form tampering, Cookie tampering, unvalidated inputs, SQL injection, Buffer overflow attacks. Information related to the target server is collected from various sources like From websites WHOIS information Netcraft information Banner grabbing Port scanning with Nmap. Mirroring a website using Htttrack. There are automated tools for scanning a web server and applications running on it. The results may show various threats and vulnerabilities on the target web server; these vulnerabilities may later be exploited using tools or manually. E.g. Acunetix, Nikto, Vega etc Guessing/Default passwords Brute Forcing Dictionary Attacks Update and patch web servers regularly. Do not use the default configuration. Store configuration files securely. Scan the applications running on the web server for all vulnerabilities. Use IDS and firewall with updated signatures. Block all unnecessary protocols and services. Use secure protocols. Disable default accounts, follow strict access control policy. Install Anti-virus, and update it regularly. All OS and software used should be latest and updated.
Web Server and its Types of Attacks
Introduction
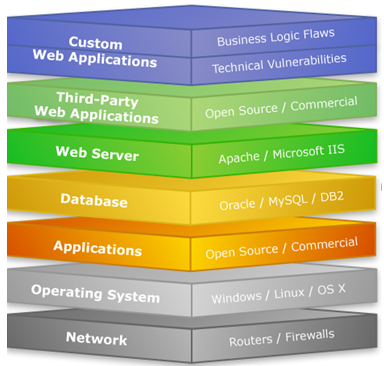
Web Server Attacks types:
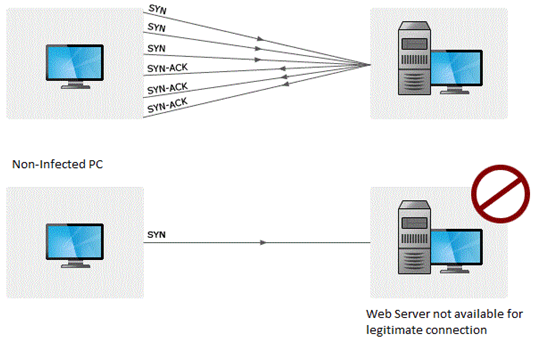
DOS attack:
Website Defacement:
Directory Traversal:
Misconfiguration attacks:
Phishing Attack:
Methodology:
Information Gathering:
Vulnerability Scanning:
Password Attacks:
Countermeasures: