The vulnerabilities in the web service protocols like SOAP, WSDL, UDDI can be exploited to do various kinds of attacks like SQL injection, XML poisoning, etc. This attack happens wherein a user is able to upload all types of file extensions even though the upload is intended only for few extensions. This is due to improper validation against the type of files getting uploaded, an attacker will be able to upload malicious files. If an attacker is able to get access to the DNS files, he can modify the contents of the DNS records so that he can redirect the victim to a malicious web page, though they are requesting for a legitimate web page. DNS Server does the domain to IP resolving; so when a DNS poisoning is executed to modify the IP corresponding to a domain to some other IP, the attacker can trick the victim into browsing the pages he intended them to instead of the original ones. Poisoning can be done at cache/DNS server, or an attack can modify the IP on the fly by intercepting the traffic too.
Web Services Attacks
File Uploads:
DNS Hijacking/Poisoning:
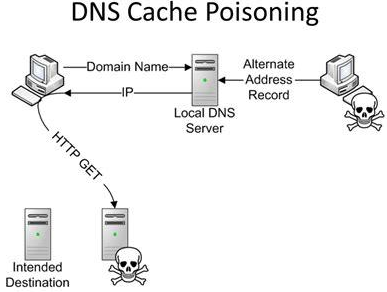
Image Source: https://commons.wikimedia.org/wiki/File:Dns-cache-poisoning.png
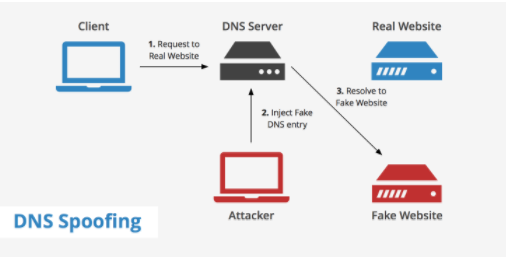
Image Source: https://www.keycdn.com/support/dns-spoofing/