Wi-Fi Attacks
Major Wi-fi attacks are done by setting up a rogue Access Point.
Evil Twin attack:
Here the attacker sets up a fake access point with a similar name to that of a corporate AP near the company premises. When an employee unknowingly connects to this access point thinking that to be the genuine AP of the company, he/she gives away the authentication details of the original access point. The attacker, thus, is able to compromise the connection.
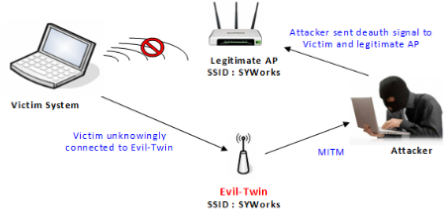
Image Source: http://syworks.blogspot.in/2014_04_01_archive.html
Jamming Signals:
An attacker can disrupt the network connection by jamming the signal, there are functioning tools for this purpose also called as creating noise.
Misconfiguration Attacks:
If a router is set up using the default configuration, weak credentials, weak encryption algorithms, then the attacker can easily break into the network.
Honey spot Attack:
An attacker can set up fake access points/hotspots with the same SSID as that of a public wi-fi AP; thus, he can set traps for the users who connect to these AP’s.
Unauthorised/Ad-Hoc connection attacks:
An attacker can enable an AD-HOC connection in a user’s system utilizing Trojan, malware, or if an employee is already using an AD-HOC connection to share the internet with peers. The attacker can compromise the connection operating in AD-HOC mode since this mode does not provide stronger encryption to the connection.
Methodology:
An attacker has to find out the wireless devices through methods like war-walking, warchalking, war-driving. There are tools like NetStumbler, Kismet to find out wireless access points and capture the traffic.
Once he captures the traffic of that connection, he has to analyse the traffic using protocol analysers to identify the authentication method used, SSID, and connected devices and how to compromise the connection.
Depending upon the protocol used for encryption, he has to follow different tools/methods to break into the network and gain access to the unauthorised network.
Countermeasures:
-
Always use WPA/WPA2 encryption.
-
Do not share your credentials.
-
Do not open untrusted emails.
-
Use IDS/Firewalls to filter the connections.
-
Change the default configurations.
-
Enable MAC-address filtering.
-
Use centralised server for authentication.
-
Do not connect to untrusted/public wifi hotspots.